AWS Regions
Regions
- all around the world
- Names / Region code (ex. us-east-1)
- Most AWS Services are region-scoped (서비스는 특정 region에 linked됨)
선택 기준
1. Compliance (with data governace and legal requirements)
2. Proximity : 사용하는 곳과 가까운 region 이용 -> reduced latency
3. Available services : 모든 Region에 모든 서비스가 있지 않음
4. Pricing : different by region
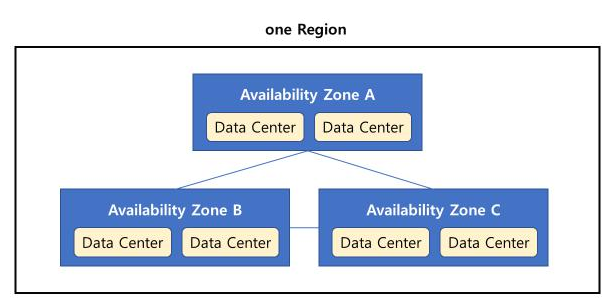
Region 구성
- Each region has many available zones(AZ) (2-6, usually 3)
- AZ is one or more discrete data centers
- separate from each other -> isolated from disasters
- connected with high bandwidth, ultra-low latenct networking
AWS Points of Presence (Edge Loactions)
- AWS for the global infrastructure is the points of presence or edge locations
- 216 Points of Presence in 84 cities across 42 countries
- Content is delivered to end users with low latency
IAM Section
IAM : Users & Groups
- IAM : Identify and Access Management (Global service)
- Root account : creatd by default
- Users & Groups : Groups contain users (cannit contain other groups)
- Users can belong to multiple groups
IAM : Permissions (Policies)
- Polices : Users/Groups can be assigned JSON documents, define the permissions
- Apply the least privilege principle
IAM Policies inheritance
In the group, users inherit the policy. If user belong to multiple groups, user inherit multi policies.
( only user, not belong to group, : inline policy)
IAM Policies Structure
- version
- Id (optional)
- Statement
- Sid (optional)
- Effect
- Principal
- Action
- Resoure
- Condition (optional)
IAM - two defense Mechanism
1. Password Policy
- Allow all IAM users to change
- password expiration
- prevent pw re-use
2. MFA (Multi Factor Authentication)
- protet Root Accounts and IAM users
- MFA = password you know + security device you own
- Main benefit : if a pw is stolen/hacekd, the account is not compromised
- MFA devices : virtual MFA devie , Universal 2nd Factor(U2F) Security Key, Hardware Key Fob MFA Device, Hardware Key MFA device for AWS GovCloud
How can users access AWS
1. AWS Management Console
2. AWS CLI
3. AWS SDK
IAM Roles for AWS Services
- IAM Roles - not by physical people, but instead by AWS Services
- Some AWS service perform actions on your behalf → assign permissions to AWS services with IAM Roles
IAM Security Tools
1. IAM Credentials Report (account-level)
: Download CSV
2. IAM Access Advisor (user-level)
: check service last accessed and Policies granting permissions
IAM Guidelines & Best Practices
- Don't use root account except for AWS account setup
- One physical user = One AWS user
- Assign users to groups and assisn permission to groups
- create strong pw policy
- use MFA
- create and use Roles to AWS services
- Use Access Keys (CLI/SDK)
- Audit permissions of your account with the IAM Credentials Report
- Never share IAM users & Access Keys
- grant least privilege
Summary
Users : a physical user, has a password for AWS Console
Groups : contains users only (cannot contains other groups)
Policies : JSON document that outlines permissions for users or groups
Roles : for EC2 instances or AWS Services
Security : MFA + Password Policy
Access Keys : access AWS using the CLI or SDK
Audit : IAM Credential Reports & IAM Access Advisor
'#️⃣ Cloud&Container > AWS' 카테고리의 다른 글
| [AWS] Colab에서 Redshift 작업시 ActiveSqlTransaction 오류해결 (0) | 2023.05.26 |
|---|---|
| AWS Redshift 톺아보기 (0) | 2023.05.25 |
| [AWS] Elastic Beanstalk 구축 실습 (0) | 2023.05.15 |
| [AWS S3 오류] Forbidden (Service: Amazon S3; Status Code: 403; Error Code: 403 Forbidden; (0) | 2023.05.11 |
| [AWS] 쉽고 빠르게 프리티어 EC2 만들기 (0) | 2023.04.24 |
AWS Regions
Regions
- all around the world
- Names / Region code (ex. us-east-1)
- Most AWS Services are region-scoped (서비스는 특정 region에 linked됨)
선택 기준
1. Compliance (with data governace and legal requirements)
2. Proximity : 사용하는 곳과 가까운 region 이용 -> reduced latency
3. Available services : 모든 Region에 모든 서비스가 있지 않음
4. Pricing : different by region
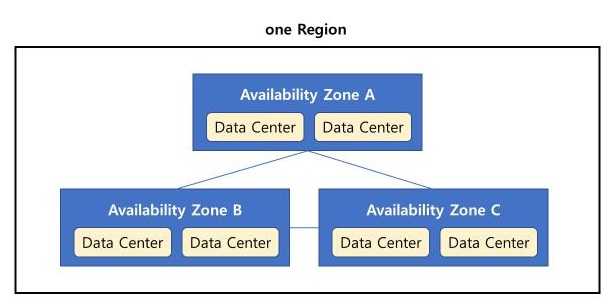
Region 구성
- Each region has many available zones(AZ) (2-6, usually 3)
- AZ is one or more discrete data centers
- separate from each other -> isolated from disasters
- connected with high bandwidth, ultra-low latenct networking

AWS Points of Presence (Edge Loactions)
- AWS for the global infrastructure is the points of presence or edge locations
- 216 Points of Presence in 84 cities across 42 countries
- Content is delivered to end users with low latency
IAM Section
IAM : Users & Groups
- IAM : Identify and Access Management (Global service)
- Root account : creatd by default
- Users & Groups : Groups contain users (cannit contain other groups)
- Users can belong to multiple groups
IAM : Permissions (Policies)
- Polices : Users/Groups can be assigned JSON documents, define the permissions
- Apply the least privilege principle
IAM Policies inheritance
In the group, users inherit the policy. If user belong to multiple groups, user inherit multi policies.
( only user, not belong to group, : inline policy)
IAM Policies Structure
- version
- Id (optional)
- Statement
- Sid (optional)
- Effect
- Principal
- Action
- Resoure
- Condition (optional)
IAM - two defense Mechanism
1. Password Policy
- Allow all IAM users to change
- password expiration
- prevent pw re-use
2. MFA (Multi Factor Authentication)
- protet Root Accounts and IAM users
- MFA = password you know + security device you own
- Main benefit : if a pw is stolen/hacekd, the account is not compromised
- MFA devices : virtual MFA devie , Universal 2nd Factor(U2F) Security Key, Hardware Key Fob MFA Device, Hardware Key MFA device for AWS GovCloud
How can users access AWS
1. AWS Management Console
2. AWS CLI
3. AWS SDK
IAM Roles for AWS Services
- IAM Roles - not by physical people, but instead by AWS Services
- Some AWS service perform actions on your behalf → assign permissions to AWS services with IAM Roles
IAM Security Tools
1. IAM Credentials Report (account-level)
: Download CSV
2. IAM Access Advisor (user-level)
: check service last accessed and Policies granting permissions
IAM Guidelines & Best Practices
- Don't use root account except for AWS account setup
- One physical user = One AWS user
- Assign users to groups and assisn permission to groups
- create strong pw policy
- use MFA
- create and use Roles to AWS services
- Use Access Keys (CLI/SDK)
- Audit permissions of your account with the IAM Credentials Report
- Never share IAM users & Access Keys
- grant least privilege
Summary
Users : a physical user, has a password for AWS Console
Groups : contains users only (cannot contains other groups)
Policies : JSON document that outlines permissions for users or groups
Roles : for EC2 instances or AWS Services
Security : MFA + Password Policy
Access Keys : access AWS using the CLI or SDK
Audit : IAM Credential Reports & IAM Access Advisor
'#️⃣ Cloud&Container > AWS' 카테고리의 다른 글
| [AWS] Colab에서 Redshift 작업시 ActiveSqlTransaction 오류해결 (0) | 2023.05.26 |
|---|---|
| AWS Redshift 톺아보기 (0) | 2023.05.25 |
| [AWS] Elastic Beanstalk 구축 실습 (0) | 2023.05.15 |
| [AWS S3 오류] Forbidden (Service: Amazon S3; Status Code: 403; Error Code: 403 Forbidden; (0) | 2023.05.11 |
| [AWS] 쉽고 빠르게 프리티어 EC2 만들기 (0) | 2023.04.24 |